Top SRE Automation Tools 2023
Using SRE automation tools in incident management is like making your system capable of living almost independently!
Using SRE automation tools in incident management is like making your system capable of living almost independently!



AWS gave customers new ways to securely and seamlessly connect their EC2 instances in the public and private subnets without the need for a bastion host, at its annual re:Inforce security conference: AWS Instance Connect Endpoint (EIC Endpoint). Thanks to EIC Endpoint, we now have SSH and RDP connectivity to our EC2 instances using private IP addresses, without using Bastion Host.
In this article, we will create step-by-step an AWS Instance Connect Endpoint to Amazon Elastic Compute Cloud (Amazon EC2) instances in private subnets and we will connect it without the need for a Bastion Host.
Also, we will talk about AWS Instance Connect Endpoint, its feature, limitations, and the ways to use it.
We will do it all step by step.

DMARC is one of the key methods for protecting your emails from spoofing. Yet, only half of Fortune 500 companies have implemented it so far. Is it because the setup is difficult? Absolutely not. Setting up DMARC is really easy and won’t take more than 15 minutes. Learn how to do it with our guide. ..

A new system call found in Linux 6.5 is 'cachestat' that allows user-space to query page cache statistics for a file in order to make more informed decisions... read more
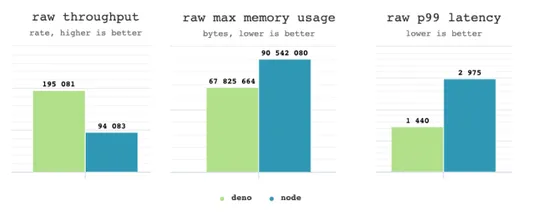
Deno's latest release brings us closer to its vision of making programming simple by offering a stable and high-performance web server API, Deno.serve(). It also improves npm support and adds highly anticipated packages, along with other improvements and bug fixes. Additionally, this release include.. read more
Computer vision is a field that aims to enable computers to understand and interpret visual data like humans do, using techniques such as the Viola-Jones algorithm for face detection and convolutional neural networks for object classification. Recent advancements include state-of-the-art object dete.. read more

Red Hat has made the decision to no longer provide the source code of Red Hat Enterprise Linux (RHEL) to the public. The code will only be available to paying customers, who are legally restricted from sharing it. This move has significant implications for downstream projects and distributions that .. read more

AI will not destroy the world and, in fact, has the potential to greatly benefit humanity by augmenting human intelligence and improving various aspects of life, from education to healthcare to scientific research. The current panic surrounding AI is driven by a combination of irrational fear and se.. read more
