Logfiles: What They Reveal and How to Use Them
Know more about logfiles, what they reveal, and how to use them for better system performance, security, and troubleshooting.
Know more about logfiles, what they reveal, and how to use them for better system performance, security, and troubleshooting.
Learn how to spot and fix Java memory leaks with practical tips, tools, and strategies to keep your application running smoothly.

Learn the basics of log parsing, from understanding logs to using the right tools, without all the technical jargon.

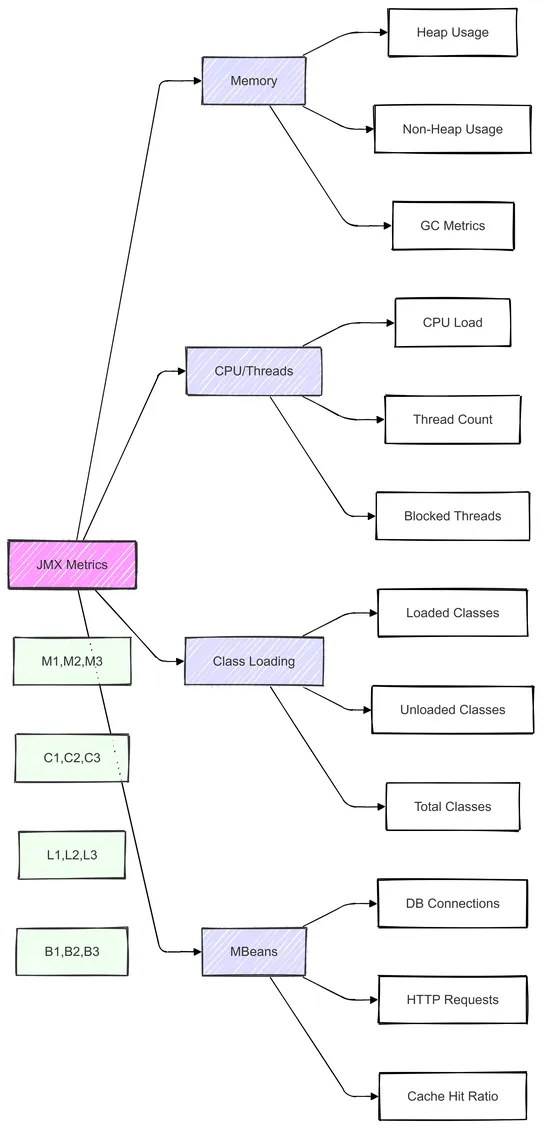
Explore JMX metrics, the types to monitor, and when to check them for optimal Java application performance and proactive troubleshooting.
The blog post provides a comprehensive analysis of 9 leading PagerDuty alternatives in 2025, focusing on pricing, features, and use cases. It begins by addressing PagerDuty's pricing pain points ($21-41/user/month plus add-ons) before diving into detailed reviews of alternatives like Squadcast ($9/user/month), Opsgenie, xMatters, and others. Each alternative is evaluated based on key features, pricing structure, and target audience. The article concludes with practical guidance on choosing the right alternative based on factors like pricing transparency, support quality, and integration capabilities. Special emphasis is placed on cost-effective options and modern features that compete with or exceed PagerDuty's offerings.
Today, we’re excited to share a diagram detailing Load Balancer Layer 4 Topologies: sNAT, dNAT, and DSR, showcasing how RELIANOID enables high performance and scalability for non-connection-oriented and real-time services. 🌐 Did you know that RELIANOID employs cutting-edge techniques tailored for d..

🚀 Network Appliances: The Backbone of Modern IT Infrastructure Network appliances like firewalls, load balancers, and VPNs are essential for optimizing, managing, and securing network traffic. They offer enhanced security, improved performance, scalability, and reliability—key to supporting growing..

This comprehensive guide explores the 10 essential incident management best practices that organizations need to implement in 2025. The article covers everything from building effective incident response teams to fostering a blameless culture, with detailed insights into the incident management lifecycle. Key highlights include establishing clear communication protocols, leveraging automation, maintaining detailed documentation, and balancing SLOs with SLAs. The guide provides practical strategies for reducing incident frequency, improving response times, and maintaining service reliability while building a resilient organizational culture.
In industries like pharmaceuticals, manufacturing, and food production, Level 3 systems are the backbone of operations. Ensuring their high availability isn't just about minimizing downtime—it's about maintaining continuous production, securing data integrity, and meeting compliance standards. Disco..

Knowing your audience is the key to a successful marketing strategy. Each segment expects to see different content to stay engaged and move closer to taking action.
So, what is B2B email marketing lead generation, and how can we make the most of it?
Here’s a tell-all on B2B lead generation through email marketing. In this tutorial, you’ll learn:
How to generate and nurture leads who are groups of stakeholders
Why email hygiene makes sales success stories in B2B
Examples of amazing lead nurturing emails in the B2B segment
Top 3 tools to streamline your B2B email marketing
