Software Load Balancers vs Appliances (Differences Explained)
Explore differences between software load balancers and appliances and learn how HAProxy's approach addresses common pain points when choosing the right form... read more
Explore differences between software load balancers and appliances and learn how HAProxy's approach addresses common pain points when choosing the right form... read more

Log monitoring is essential for system administration and cybersecurity, focusing on scrutinizing log files for system health and security. Key components include log data collection, analysis, alerting mechanisms, and visualization tools. Several log monitoring tools, such as Atatus, Papertrail, Se.. read more
Assortment of technology startup infrastructure recommendations.. read more

AWS offers a variety of cryptography services, including CloudHSM and KMS, as well as client-side software like the AWS Encryption SDK and Secrets Manager. Understanding when to use each service can help enhance the security of your cloud-based applications... read more

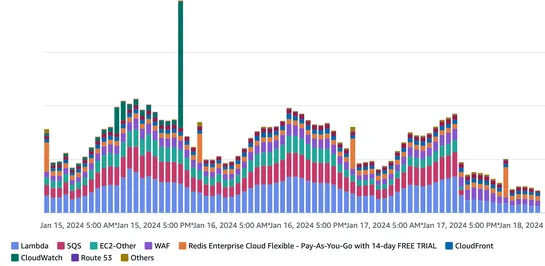
By focusing on different areas of their AWS infrastructure, this company was able to cut costs by $109,459 per year. They made changes to CloudWatch, NAT Gateway, S3, Route53, Lambda, SQS, WAF, and CloudFront to achieve these significant savings... read more
AWS recently enhanced the management of Kubernetes service EKS with an introduction to IAM identities for users/roles, improving application authentication and access to AWS resources. This enhancement offers significant benefits but also potentially opens new avenues for exploitation by malicious a.. read more
Discover the best incident management software of 2024 for every business size, from Squadcast to Moogsoft, with features and pricing to guide you

Salesforce projects can be exciting endeavors, promising significant rewards for both your business and your customers. However, navigating through these projects requires careful planning and execution.

When Google first launched, people typing in the search query “please give me today’s weather” would be considered unusual, because that’s what it was a query. “You don’t talk to a computer!” was the generally accepted view. Slowly and steadily, these queries have been moving closer and closer to questions.
“Natural Language Processing” was the key phrase. The goal was that the systems to be able to understand how people talk in their regular daily life. The complex neural networks, machine learning algorithms were developed for this purpose. The idea is that instead of teaching the computer how to understand, we give it the tools to learn how to understand. We take humans out of the equation. Instead of teaching it languages, we teach the computer how to detect patterns and learn from those patterns it themselves, occasionally intervening to tweak the importance, the weight, given to each data source point. Read more: https://cloudzenix.com/the-gold-rush-of-ai-systems-has-just-begun/

Information security activities are always integral to the Security Operations Center (SOC). The SOC team usually analyzes and monitors the security systems in an organization. Protecting the business from unprecedented security breaches is the end goal of a SOC professional; they make it happen by identifying, discovering, analyzing, and responding to cybersecurity threats. DevSecOps Solutions cloud have a significant impact on how SOCs operate in 2023.
SOC comprises administrators, security engineers, and security analysts, and they collaborate with IT operations and internal development teams to ensure security breaches are at bay. SOC does come with several challenges while protecting the organization’s assets from unprecedented cyber threats, ensuring that all systems in IT infrastructure, such as the systems and networks, have protection throughout the year. Read more: https://cloudzenix.com/is-devsecops-solutions-on-verge-to-replace-the-soc/
