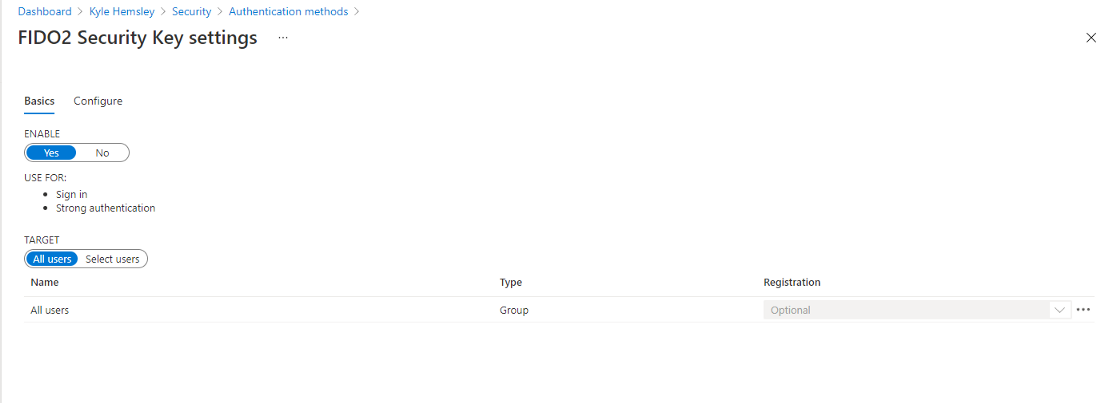
Most however never leverage it beyond default settings, or even disable security defaults to appease less security conscious employees. Azure AD out of the box does not offer passwordless authentication, but can be configured to support it via the Azure Active Directory Authentication Methods management blade found at Authentication methods — Azure Active Directory admin center. This step is necessary before any user can add FIDO2 key.
Note that FIDO2 keys function as passwordless authentication and not password + MFA. When the user attempts to log into an Azure Active Directory application (Outlook, OneDrive, SharePoint, third party apps w/ SSO), they are not prompted for a password. Instead they are prompted to insert their security key, enter a PIN which is used to unlock the key, and then touch it to authenticate with the security device’s cryptographic key. It also does not work on all browsers / platforms but support is fairly broad at this point, Microsoft’s limitations are specified here Browser support of FIDO2 passwordless authentication | Microsoft Docs.