
Azure AD is a powerful cloud-based IdP from Microsoft that many organizations have “free” access to through their M365 subscriptions for Office 365 / Exchange Online.
Most however never leverage it beyond default settings, or even disable security defaults to appease less security conscious employees. Azure AD out of the box does not offer passwordless authentication, but can be configured to support it via the Azure Active Directory Authentication Methods management blade found at Authentication methods — Azure Active Directory admin center. This step is necessary before any user can add FIDO2 key.
Note that FIDO2 keys function as passwordless authentication and not password + MFA. When the user attempts to log into an Azure Active Directory application (Outlook, OneDrive, SharePoint, third party apps w/ SSO), they are not prompted for a password. Instead they are prompted to insert their security key, enter a PIN which is used to unlock the key, and then touch it to authenticate with the security device’s cryptographic key. It also does not work on all browsers / platforms but support is fairly broad at this point, Microsoft’s limitations are specified here Browser support of FIDO2 passwordless authentication | Microsoft Docs.
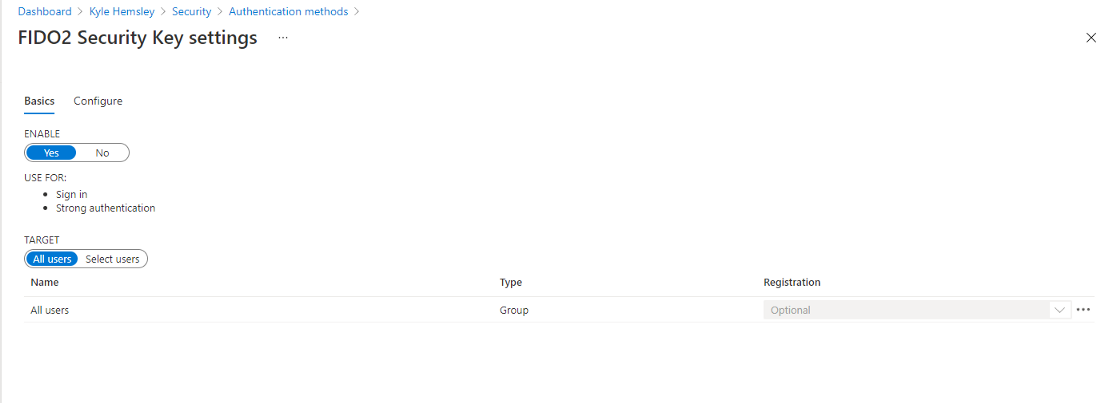
To enable FIDO2 keys, scope down into the FIDO2 menu in Authentication Methods, and enable it with a target of either all users or specified groups. In the configure tab, it is possible to blacklist or whitelist certain devices by their AAGUID, which is useful if attempting to require a device such as the YubiKey Bio. Yubico’s list of AAGUID’s can be found here YubiKey Hardware FIDO2 AAGUIDs — Yubico if you wish to only allow certain models or block undesirable ones.
Once this is done, users can enroll keys for passwordless authentication via the standard Azure AD authenticator enrollment URL https://aka.ms/mfasetup. They will need to select “security key” in the dropdown. After completing this, I would recommend phone numbers be removed, especially for senior staff and executives due to the risk of targeted account theft. If criminals can convince mobile carrier customer service to transfer Jack Dorsey’s phone number, they can do the same for yours.
I ended up removing my phone number as a result of this concern. Having only a single method however is not recommended as it presents a risk of account loss until an administrator can restore access. In the event of losing access to the only administrator account, this involves a long process with Microsoft Support. Note that Yubico recommends enrolling a spare key and storing it safely, which I chose to follow. However, enrolling another secure authentication method like Microsoft Authenticator — Apps on Google Play / Microsoft Authenticator on the App Store (apple.com) is enough to prevent account lockout due to a broken or lost security key / smartphone.
It is also possible to do passwordless authentication with Microsoft’s mobile app — which is a separate trip to the Authentication Methods console and its own implementation caveats such as requiring Azure AD device enrollment of the smartphone — enabling MDM if your tenant has Intune configured. With passwordless authentication, it is also possible to log into Windows 10 or 11 on an Azure AD joined laptop or workstation. Through Conditional Access policies, it is even possible to disable traditional password sign-in entirely.
I hope this article has been a helpful look into the passwordless capabilities of Azure Active Directory and the power of FIDO2 keys. I use a YubiKey 5C that I purchased during the Black Friday sale. This is an especially powerful authentication model for an M365 account tied to a kiosk / shared special purpose computer. Through Conditional Access, that account can be locked to a single usage location and require employees to present their individual security key to log in. When an employee is offboarded, their key can be physically retrieved and/or removed from the user’s authentication methods, which is a far more elegant model than changing the shared account’s password. It is of course also a powerful security tool for normal user accounts, and can be more convenient than traditional password logins.
Start blogging about your favorite technologies, reach more readers and earn rewards!
Join other developers and claim your FAUN account now!
User Popularity
51
Influence
5k
Total Hits
1
Posts
















Only registered users can post comments. Please, login or signup.