I am a DevOps engineer at Cloudify.co and I will share in this post my experience related to automation of Vault backup creation using Jenkins scheduled job and simple python script which I built to create dump of vault secrets.
Let’s start.
What is HashiCorp’s Vault?
Vault is a tool for securely accessing secrets. A secret is anything that you want to tightly control access to, such as API keys, passwords, certificates, and more. Vault provides a unified interface to any secret while providing tight access control and recording a detailed audit log.
https://www.vaultproject.io/
What is Jenkins Pipeline?
Jenkins Pipeline (or simply “Pipeline” with a capital “P”) is a suite of plugins that supports implementing and integrating continuous delivery pipelines into Jenkins.
https://www.jenkins.io/doc/book/pipeline/
Prerequisites:
- Vault Installed
- Jenkins Installed
My Setup
- EKS Kubernetes cluster
- Vault runs on EKS cluster
- Jenkins runs on EKS cluster
You can read in this tutorial how to run Jenkins on EKS cluster:
https://igorzhivilo.com/jenkins/ci-cd-future-k8s-jenkins/
What you will learn from this post?
- How to use python hvac library for authentication with Vault programmatically and backup vault secrets.
- What is AppRole authentication mechanism in Vault and how to enable/create it?
- How to create a scheduled backup for Vault secrets with Jenkins pipeline on k8s.
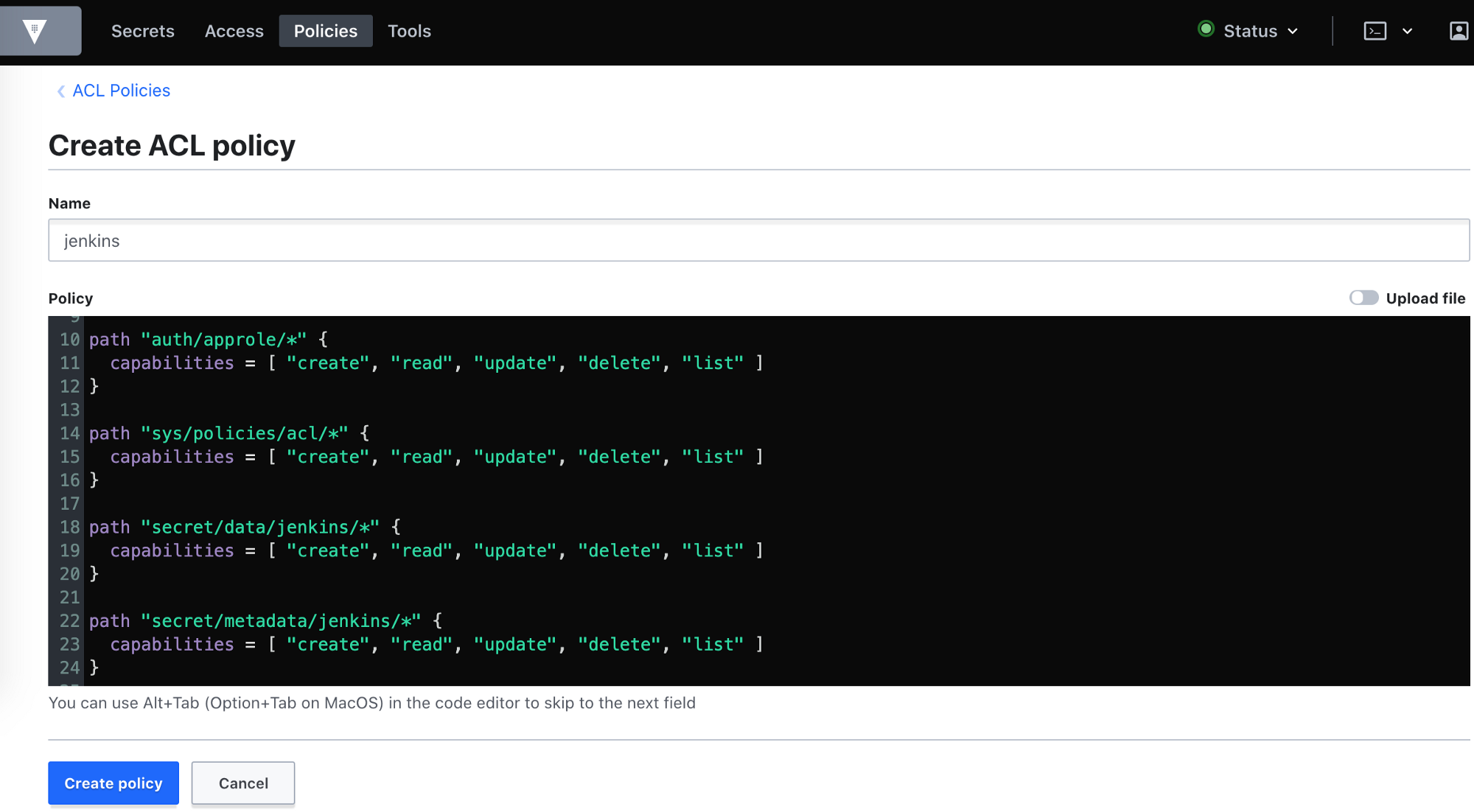
AppRole authentication method in Vault
How can an application programmatically request a token so that it can read secrets from Vault?
Using the AppRole which is an authentication mechanism within Vault to allow machines or apps to acquire a token to interact with Vault and using the policies you can set access limitations for your app.
It uses RoleID and SecretID for login.