Is Ether the Next Anime NFT Blue Chip?
The highly anticipated anime-style NFT project with impressive art, passionate community, and ambitious vision, poised for success... read more
Join us
The highly anticipated anime-style NFT project with impressive art, passionate community, and ambitious vision, poised for success... read more
Hey, sign up or sign in to add a reaction to my post.
The author reflects on the challenges and decisions faced in the crypto community over the past five years. They discuss the complexities of designing systems and the trade-offs made, using examples like the choice of push oracles over pull oracles. The article explores the dynamics between DAOs and.. read more
Hey, sign up or sign in to add a reaction to my post.
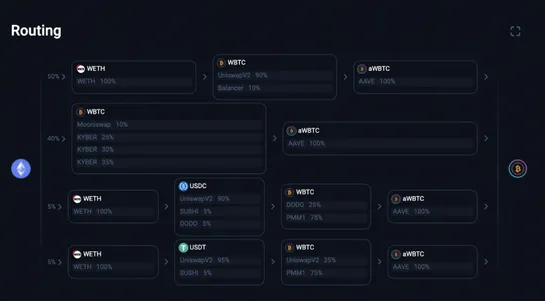
These powerful decentralized exchange platforms are the search engines of DeFi.. read more
Hey, sign up or sign in to add a reaction to my post.
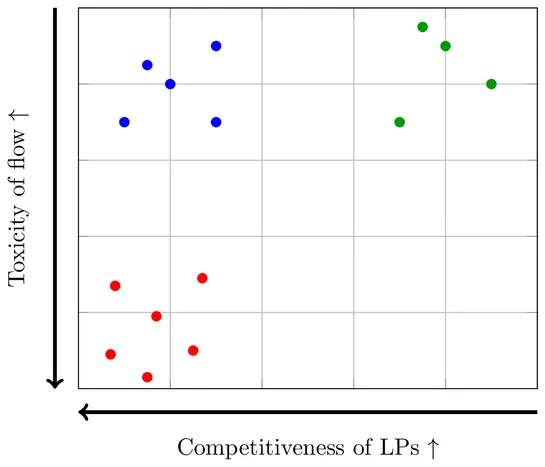
New research introduces FLAIR, a metric to calculate LP performance that includes LPs competing for trading fees within the same pool... read more
Hey, sign up or sign in to add a reaction to my post.
Soft rug pulls are a common type of scam in the cryptocurrency space. Unlike hard rug pulls, which involve malicious code or exploits, soft rug pulls are solely social engineering attacks... read more

Hey, sign up or sign in to add a reaction to my post.
Discover the power of AWS KMS and how it seamlessly integrates with EBS volume encryption to enhance data security. Learn about data key generation, the role of the hypervisor, secure key storage, and the benefits of key policies for access control.

Hey, sign up or sign in to add a reaction to my post.
While Salesforce’s testing capabilities are sufficient for running small deliverability tests or previewing your emails, they may not be enough for inspecting and debugging emails in detail. Plus, some methods may bear the risk of spamming contacts with test emails. That’s where Mailtrap Email Testi..
Hey, sign up or sign in to add a reaction to my post.
This blog will demystify Kubernetes by breaking down its core components, revealing its operational principles, and guiding you through the process of running a pod. By the end of this blog, you will have a solid understanding of Kubernetes and be equipped to harness its capabilities effectively.

Hey, sign up or sign in to add a reaction to my post.
Service Accounts are useful but, if not properly managed, they can pose security risks. Read the article to learn how to securely use a Service Account!

Hey, sign up or sign in to add a reaction to my post.
This organization doesn't have a detailed description yet. If you are the administrator of this organization, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way to stay updated with what's happening in the tech world.
We sift through mountains of blogs, tutorials, news, videos, and tools to bring you only the cream of the crop — so you can kick back and enjoy the best!
