NeuVector: Automating and Shifting Security Left in Kubernetes
Security Policy as Code (SPaC): Shifting Security Left with NeuVector
Shifting security left, a practice that integrates security into the development process from the early stages, is at the core of DevOps, DevSecOps, and modern Cloud Native practices. However, implementing it is not always easy and straightforward, and if the implementation is not done correctly, it can lead to friction between security and development teams and slow down the development process. NeuVector's Security Policy as Code (SPaC) feature is designed to address these challenges by providing a way to define security policies in code, which can then be shared with development teams to ensure that security is integrated into development, CI/CD pipeline, and testing processes.
In the previous section, we have seen how NeuVector can enforce security policies using the Discover, Monitor, and Protect modes. NeuVector's SPaC feature allows you to define these policies in a declarative way using YAML files. For example, when we deployed WordPress, NeuVector automatically created a group with a set of observed rules. We added a new rule to whitelist the HTTPS/SSL connection, and we considered that these are the final set of rules that we want to enforce. We can then export it to a YAML file and share it with the development team to ensure that the same enforcement is consistently applied across all environments, especially in the earlier stages of the SDLC, and that the same will be shipped with the application.
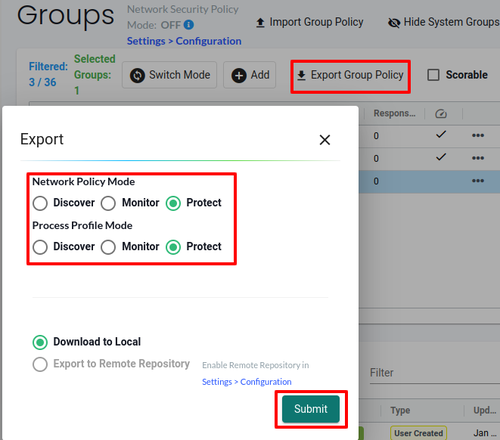
To do this, using the UI, navigate to the Groups tab, select the group you want to export the rules from, click on Export Group Policy, select the mode (Discover, Monitor, or Protect), and click on Submit. This will generate a NvSecurityRule CRD manifest.
Export Group Policy
Following is a partial example of an NvSecurityRule CRD manifest exported for the nv.my-wordpress.wordpress group that specifies the security policies, including allowed network traffic (ingress and egress), permitted processes, and other security settings like DLP and WAF.
# Define the API version and the type of resource
apiVersion: neuvector.com/v1
kind: NvSecurityRule
# Metadata about the security rule
metadata:
# Name of the security rule
name: nv.my-wordpress
# Kubernetes namespace where the rule is applied
namespace: my-wordpress
spec:
# Enable Data Loss Prevention (DLP) features
dlp:
status: true
# Enable Web Application Firewall (WAF) features
waf:
status: true
# Define outbound (egress) network traffic rules
egress:
# Allow outgoing DNS traffic
- action: allow
applications: [DNS]
name: allow-dns
ports: any
selector:
criteria:
- key: service
op: =
# Match the CoreDNS service
value: rke2-coredns
# Define inbound (ingress) network traffic rules
ingress:
# Allow incoming SSL traffic on port 443
- action: allow
applications: [SSL]
name:End-to-End Kubernetes with Rancher, RKE2, K3s, Fleet, Longhorn, and NeuVector
The full journey from nothing to productionEnroll now to unlock all content and receive all future updates for free.