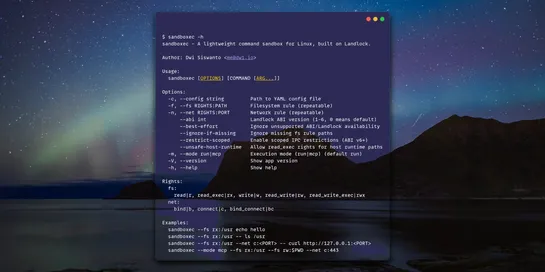
The most practical, fast, tiny command sandboxing for AI agents
Need to run one sketchy command without a full container? Here is the most practical, lightweight way to lock down one risky command in your AI pipeline. No daemon, no root, no image build.