Practical MCP with FastMCP & LangChain
Engineering the Agentic Experience

FastMCP 3.0 is now generally available. It keeps the @mcp.tool() API but rebuilds the internals around components + providers + transforms, adds a CLI, and ships production features like component versioning, per-component auth + OAuth additions, OpenTelemetry tracing, background tasks, pagination, tool timeouts, and hot reload. The project moved from jlowin/fastmcp to PrefectHQ/fastmcp on GitHub, and upgrading is supported via dedicated guides for FastMCP 2 and MCP SDK users.

Join us at London OWASP Training Days 2026 – February 25–28 in London! Hands-on, instructor-led sessions covering: 🔹 API Security 🔹 Secure Development & Testing 🔹 Threat Modeling & Risk Analysis 🔹 AI & Security 🔹 Mobile & IoT Security 🔹 Offensive Security & Pentesting Learn from the global OWASP com..

Downtime isn’t just costly—it’s a trust killer. 💸 In financial services, outages can cost millions, invite regulatory penalties, and damage customer confidence. Our latest blog dives into the true cost of downtime and why resilience, security, and compliance must be non-negotiable. #FinancialServic..

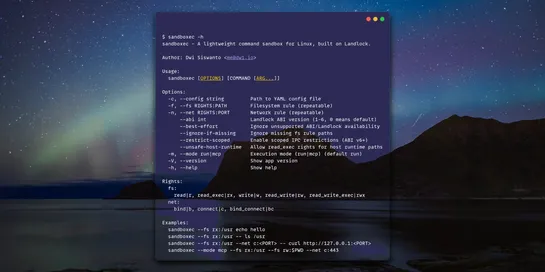
Need to run one sketchy command without a full container? Here is the most practical, lightweight way to lock down one risky command in your AI pipeline. No daemon, no root, no image build.
⚡ Infrastructure ready in minutes ⚡ Official Terraform module ⚡ Fully automated Azure deployment Simple. Fast. Reproducible. #Terraform#Azure#DevOps#IaC#LoadBalancer#CloudInfrastructure#RELIANOID https://www.relianoid.com/resources/knowledge-base/community-edition-v7-administration-guide/deploy-reli..
🚀 See you at DeveloperWeek — February 18–20, 2026! The world’s largest independent software development & AI engineering conference lands in San Jose, bringing together developers, architects, and tech leaders shaping the future of software. From AI & cloud-native to DevSecOps and developer experien..
Peter Steinberger, creator of OpenClaw, is joining OpenAI to work on bringing AI agents to a broader audience, while OpenClaw will move to an independent open-source foundation and continue development outside OpenAI’s direct control.
