Interpreting Software Testing Metrics Beyond Dashboards
Learn how to interpret software testing metrics beyond dashboards, turning raw data into actionable insights that improve release decisions and reduce risk.
Join us
Learn how to interpret software testing metrics beyond dashboards, turning raw data into actionable insights that improve release decisions and reduce risk.

Do not wear on production deployment days, mate! This t-shirt feels soft with the right amount of stretch. It's comfortable and smooth. ✅ 100% cotton ✅ Classic fit ✅ Tear-away label ✅ Runs true to siz...

The best email APIs for Python developers are Mailtrap, Mailgun, SendGrid, Amazon SES, and Postmark. SDK quality & framework compatibility All five providers offerPythonSDKs and they’re compatible with popular frameworks. I tested each withDjango,Flask, and FastAPI to assess real-world integration. ..
In today’s hyper-connected world, digital supply chains are only as secure as their weakest link. One single vendor can open the door to ransomware, outages, or worse. At RELIANOID, we take this risk seriously. 🔒 That’s why we apply: ✅ Continuous vendor risk assessments ✅ Real-time monitoring of thi..

Cybersec Asia is coming to Bangkok on February 4–5, 2026 — the key APAC event for cybersecurity, cloud, and data protection. 🌏 Bringing together global and regional leaders to tackle evolving threats and unlock new opportunities across CLMVT & APAC. 🤝 Meet RELIANOID and discover how we deliver secur..

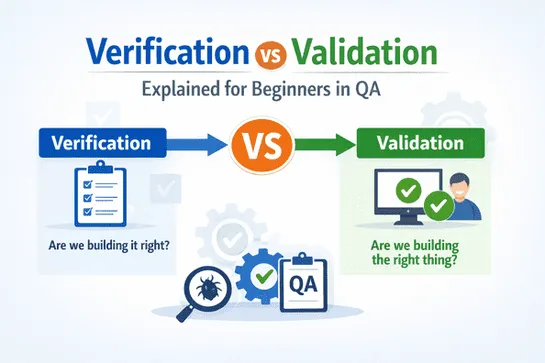
Learn the difference between verification vs validation in QA. This beginner-friendly guide explains how both ensure software is built correctly and meets user expectations.
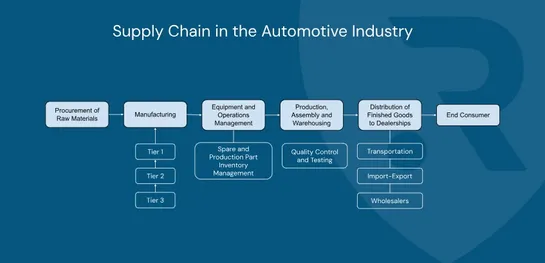
We originally published this article back in November, but it remains highly relevant today. Sharing it again in case you missed it 👇 Connected cars are no longer just mechanical machines — they are computers on wheels, embedded in complex digital ecosystems. As shown in the “Supply Chain in the aut..
Financial institutions continue to face rising cyber risks—not just from direct attacks, but from the vast networks of third-party suppliers that support their operations. Recent industry analyses reveal critical insights: Many essential vendors are far more important than organisations realise. ..
Do you also wonder, “Are AI detectors accurate?” and think the answer is a simple yes or no? The problem lies in the expectation. AI detectors don’t work like switches. They assign a probability of the text being AI-generated. The job of an AI detector is to estimate the likelihood, not to give verdicts.

the $26 billion losses caused by global tech outages in 2025 highlight a hard truth — our digital infrastructure is more fragile than we’d like to believe. In this article, I dive into the real impact of these failures, the key lessons for businesses, and how RELIANOID actively contributes to preven..
At RELIANOID, security is not just a feature — it’s a design principle. Our load balancing platform and organizational controls are aligned with ISO/IEC 15408 (Common Criteria), the internationally recognized framework for evaluating IT security in government and critical infrastructure environments..
