Cloudflare Turns Workers into an Email Platform - Private Beta Begins.
Cloudflare introduces a private beta for its Email Service, integrating email sending into Workers to streamline email management and enhance delivery reliability for developers.
Join us
Cloudflare introduces a private beta for its Email Service, integrating email sending into Workers to streamline email management and enhance delivery reliability for developers.

Hey, sign up or sign in to add a reaction to my post.
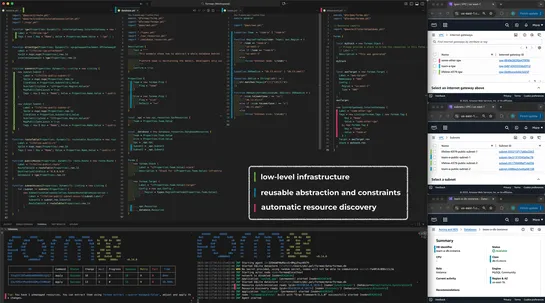
Platform Engineering Labs introduces formae, an open-source IaC platform, to streamline cloud resource management and replace traditional systems like Terraform.
Hey, sign up or sign in to add a reaction to my post.
An AWS outage disrupted Eight Sleep's smart beds, prompting plans for an "outage mode" to enhance system resilience and prevent future connectivity issues.

Hey, sign up or sign in to add a reaction to my post.
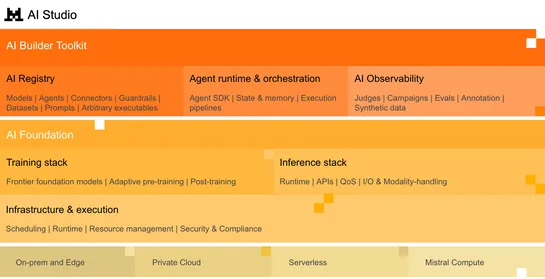
Mistral AI Studio launches to aid enterprise AI teams in moving from prototypes to production with enhanced infrastructure and governance features.
Hey, sign up or sign in to add a reaction to my post.
GitLab 18.5 introduces a new panel-based UI and AI-driven tools to enhance usability, streamline workflows, and improve security with features like automated vulnerability triage and Static Reachability Analysis.

Hey, sign up or sign in to add a reaction to my post.
- We’re excited to announce the launch of RELIANOID 8.4, bringing greater performance, security, and automation to your Application Delivery Infrastructure. - What’s new in 8.4: - High-Performance Proxy – Now with HTTP/2 support and Hot Restart for seamless, zero-downtime updates. - Multi-Factor Aut..

Hey, sign up or sign in to add a reaction to my post.
Understand how OpenTelemetry Spans capture, connect, and explain every operation in your distributed system for deeper visibility.

Hey, sign up or sign in to add a reaction to my post.
This tool doesn't have a detailed description yet. If you are the administrator of this tool, please claim this page and edit it.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way for busy developers to keep up with the technologies they love 🚀
