DevSecOps in Practice
A Hands-On Guide to Operationalizing DevSecOps at Scale
Join us
A Hands-On Guide to Operationalizing DevSecOps at Scale

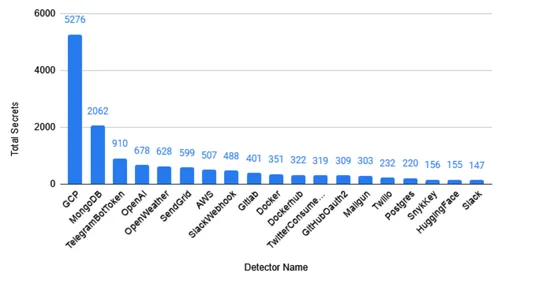
A security research project led by Luke Marshall scanned 5.6 million GitLab repositories, uncovering over 17,000 live secrets and earning $9,000 in bounties, highlighting GitLab's larger scale and higher exposure risk compared to Bitbucket.
Hey, sign up or sign in to add a reaction to my post.
Hey there! 👋
I created FAUN.dev(), an effortless, straightforward way for busy developers to keep up with the technologies they love 🚀
