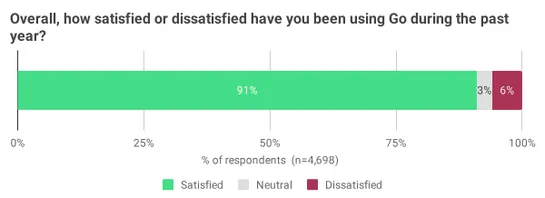
SSH has no Host header
A dev built a custom SSH proxy that punches through IPv4 limits without handing out public IPs like candy. Their trick:shared IPv4s with per-user relative IP mapping. It maps incoming SSH traffic to the right VM using thesource IPandpublic key combo. No Host header? No problem. They sidestep that ho.. read more