AI and QE: Patterns and Anti-Patterns
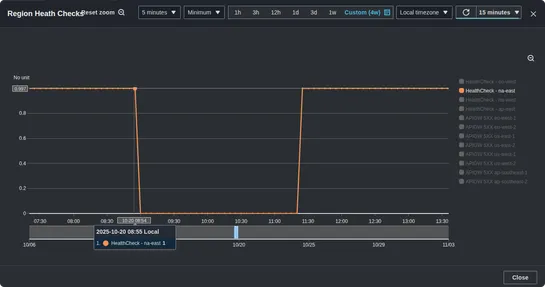
The author shared insights on how AI can be leveraged as a QE and highlighted potential dangers to watch out for, drawing parallels with misuse of positive behaviors or characteristics taken out of context. The post outlined anti-patterns related to automating tasks, stimulating thinking, and tailor.. read more