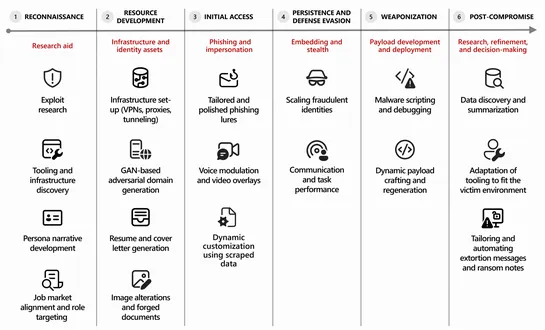
pg_plan_alternatives: Tracing PostgreSQL’s Query Plan Alternatives using eBPF
The tracer hooks PostgreSQL's optimizer via eBPF. It captures every alternative plan path with cost estimates and flags the chosen plan. A kernel-space eBPF program reads planner structs using DWARF-derived offsets. A user-space collector gathers the data and a visualizer renders plan graphs. eBPF p.. read more