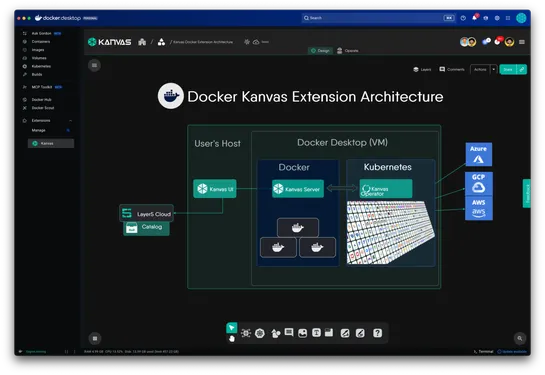
14x Faster Faceted Search in PostgreSQL with ParadeDB
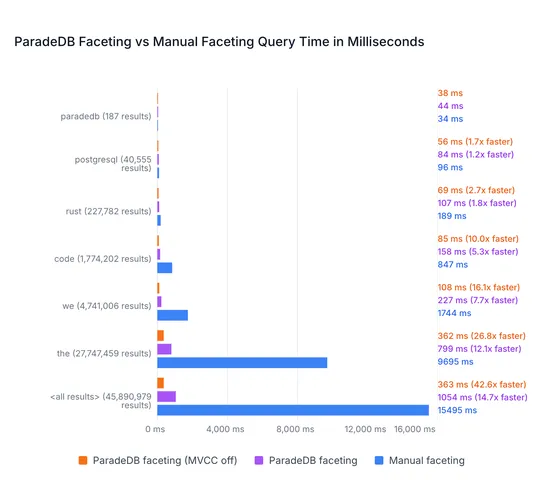
ParadeDB brings Elasticsearch-stylefacetingtoPostgreSQL, ranked search results and filter counts, all in one shot. No extra passes. It pulls this off with a customwindow function, planner hooks, andTantivy's columnar index under the hood. That's how they’re squeezing out10×+ speedupson hefty dataset.. read more